On December 20, the U.S. Financial Industry Regulatory Authority (FINRA) published its Report on Selected Cybersecurity Practices (Report), describing effective practices that it has observed among the broker-dealer firms that it supervises. Cybersecurity continues to be a high priority, regulatory compliance issue north of the border, and so we think that the Report is a worth a read for Canadian registrants, too. Based on the report, we’ve outlined some questions below for firms to consider:
Mobile devices: The proliferation of mobile devices increases the risk of data loss. Does your firm have appropriate policies and procedures to regulate risk for mobile devices used by employees, such as bring-your-own-device standards, security settings, encryption, passwords, physical security, reporting procedures for lost devices, and capacity to remotely wipe firm data for devices that have been lost or belong to former employees? Depending on their business model, firms also should consider whether there are steps they should take regarding their customers, such as:
- monitoring mobile application markets on the dark web for malicious applications that impersonate the firm’s mobile application;
- informing customers about the risks of accessing and storing personal and financial data on their mobile devices; and/or
- restricting certain changes to account settings via mobile device and requiring customers to contact the firm to make such changes.
Insider threats: Either intentionally due to malicious behavior or inadvertently (e.g., a laptop lost in a Lyft), insiders pose a serious threat to cybersecurity. Does your firm have the right amount of technical controls (including effective identity access management and user entitlement processes), additional controls for privileged users, data loss prevention (DLP) controls (i.e., that identify sensitive customer or firm data and then block or quarantine its transmission), training, measures to identify potentially abnormal user behaviour in the network, and adequate supervision?
Penetration testing: Testing cybersecurity policies and procedures is an important part of any compliance program. Would penetration testing (i.e., a simulated attack on the firm’s computer network) to validate your policies and procedures be appropriate for your firm? One factor to consider in assessing the relevance of penetration testing (and which type of test, if any, should be conducted) is the degree to which the firm manages or stores confidential or critical data such as trading strategies, customers’ personal information, and/or confidential information about other entities (such as information about mergers and acquisitions).
Branch Controls: Does your firm have more than one office? If so, it may be appropriate for you to assess:
- Whether you have adequate cybersecurity policies, procedures and technical controls that address the risks arising from branch office structures;
- The quality of your asset inventories (e.g., that identify where sensitive customer and firm information is stored) and whether you’re ensuring security of physical assets and providing for secured asset disposal at your branches;
- Whether your reviews of branch office operations encompass compliance with cybersecurity policies and procedures.
Even if you don’t have branch offices, some of the considerations listed in the Report relating to branch offices (e.g., ensuring minimum encryption standards as well as regular patching, anti-virus and malware protection and operating system updates for hardware used to access firm systems) may be relevant if you have employees that work remotely.
Phishing: Social engineering or “phishing” attacks continue to be one of the most common cybersecurity threats faced by firms. Measures a firm may wish to consider taking to address these risks include the following:
- Do you have appropriate technology in place to prevent as many attacks as possible and reduce the impact of successful attacks? In our view, it’s not a question of if your firm will be hit. It’s a question of how prepared you are.
- Do you including phishing scenarios in the firm-level, risk assessment process?
- Do you conduct regular, simulated phishing campaigns to evaluate employee understanding of and compliance with firm policies and procedures?
- Do you conduct remedial training and impose appropriate consequences for employees who repeatedly violate the firm’s policies or do not demonstrate sufficient sensitivity to phishing risks during the firm’s simulated phishing campaigns?
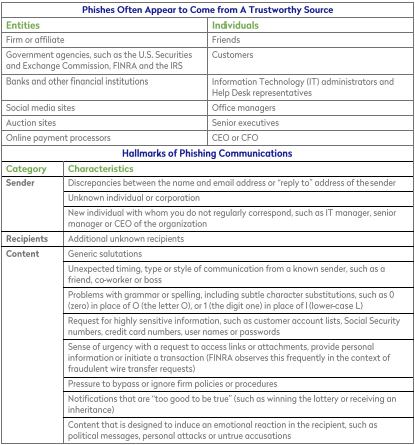
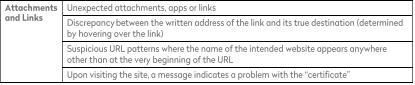
The Report includes a pair of useful charts to remind readers of: (1) the kinds of trustworthy entities or individuals that attackers often seek to disguise themselves as; and (2) the hallmarks of phishing communication. When you read these reminders, it’s hard not to say, “Duh, that’s obvious.” But it’s surprisingly easy to forget the obvious when a well-crafted phishing email pops up on your screen. So, for your convenience, we’ve reproduced the charts for you below, so that you can pin them to your bulletin board.